喜马拉雅xm文件解密逆向分析 [Electron]
How did I miss an interview
In Feb.6 2022. I miss the interview with ****(name reducted). The reason for that is that my calendar had its sheduled interview time at 12:30 instead of 11:30.The event in the calendar was automatically added using an todo list application (a sub module of FMA) written by myself, so there must be a hidden bug I didn't find.
Debugging
I first analyze the process of event synchronization. There are basically two stage, the first stage is parsing, the second stage is send request to calendar api.
I first test calendar api using an unit test I've already written. Everything works fine.
So, the problem occurs in time parsing stage.
After running another unit test, I found out there was a bug in time conversion. I forgot to change timezone value
// to unix time
currentTime.Add(time.Hour*(-7))because In Canada, there is a daylight saving time. In winnter, it is actually -8 instead of -7!
As a result, the calculated time is one hour later than the actual time.
Fixing
// to unix time
currentTime.Add(time.Hour*delta)Lesson Learned
Never use your own application in real shit
Breaking PrairieLearn Java Grader
PrairieLearn Java Autograder Vulnerability
Aynakeya aynakeya.official@gmail.com
Abstract
This is a walkthrough of one vulnerability I found in PrairieLearn Java autograder.
The default Java autograder exists vulnerabilities that allow user to leak information and write files to the container.
These vulnerabilities allow the user to modify the result of autograder score and get 100% without writing any actual code.
Vulnerability has been fixed in commit 7871ce5
Since the vulnerability hasn't been fixed yet. Anyone who read this document should not disclose the content of the vulnerability
to public in any form until the vulnerability is fixed and deployed to production.
MagicEXIF破解思路之VB程序破解
从0开始的VB程序破解
上周,为了整点乐子,我打算寻找一个简单的软件来进行破解。正好某群友有一个需要破解的应用,于是这个应用就不幸的成为了我的目标。
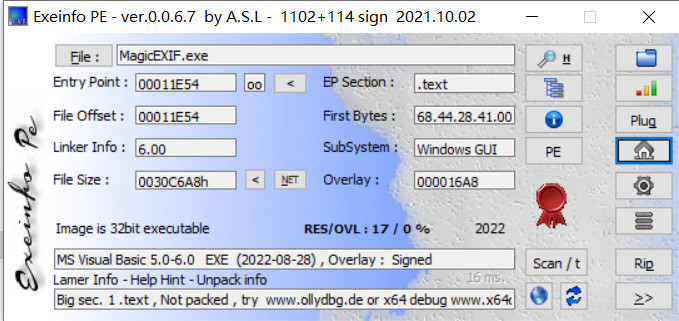
开始之前先来介绍一下这个程序,MagicEXIF一个非常强大的图片元数据编辑器。 分为免费版,专业版,旗舰版。
安装完程序后,先来看看程序的基本信息
Piping In Linux
Linux piping in summary
| Symbol | Purpose |
|---|---|
| |
pipe standard out from one program to standard input of another |
< |
redirect standard in from a file |
> |
redirect standard out to a file, deleting its current contents |
&> |
redirect both standard out and standard error to a file, deleting its current contents |
>> |
redirect standard out to a file, adding to the end of tis current contents |
&>> |
redirect both standard out and standard error to a file, adding to the end of its current contents |
CSAW CTF 2022 决赛记
A Brief Introduction of Seccomp and How to Bypass it
Introduction
I have solve several seccomp related challenges in past few ctfs. To further enhance my understanding on seccomp, I decide to take a some time and learn how seccomm works.
All the codes used in this post can be download from here seccomp.zip
Seccomp
So whats is seccomp? "Seccomp is a computer secuirty facility in Linux kernel.[1]"
Basically, seccomp create a sandbox which limit user's ability to use syscalls. Using seccomp, we can create a environment that allow/disallow specific syscall being used.
The first version seccomp released at 2005. At that time, seccomp only have one node: strict mode. In this mode, users are only allowed to use four type of syscall read, write, exit and sigreturn. In strict mode, if user use any of syscall other than those four, the program will terminate immediately. (This is not very useful because there are too many limits!)
Then, in 2012, the second version of seccomp was introduced. Now seccomp have a new mode called filter mode. In this mode, user can specify syscalls that are allowed to run using BPF (Berkeley Packet Filter) virtual machine.
[动漫碎碎念] 简评2022年七月番
七月,本来计划着在暑假里多看点动漫的我,挑挑选选,最后还是只看了两部原创动漫,《Lycoris Recoil》和《Engage Kiss》。